Table of Contents
Introduction
To put it simply, organizations depend on data to operate. From day-to-day operations to strategic decisions, data keeps an organization ticking. The volume of data is immense, and data growth is explosive. And with all that scale and explosive growth comes data security challenges. As the pioneer behind Data Security Posture Management (DSPM), Symmetry System’s DataGuard is redefining what a data-centric approach to cybersecurity looks like—security from the data out, not the perimeter in—using a deployment approach that can examine data in different environments: the cloud, on-prem, or both. Using information gleaned from millions of customer data points, this document presents the eight most common data security challenges that TBC regularly sees. We discuss how eight issues happen, the risks associated with them, and the remediations and best practices to improve overall data security. Highlights include:
Data Security Posture Management
DSPM directly addresses the issues security, data, and IT teams have related to understanding the details associated with sensitive data—who has access, how it is being used, where it’s located, and how safe it is. DSPM is about data visibility—first by identifying data at the data object level, mapping which identities that have access to what data, and then exploring how the data flows across the environments.
The Zero Trust Component
Comprehensive DSPM solutions like DataGuard accelerate Zero Trust adoption by providing SecOps, InfoSec, IT, and data teams accurate insight into who has access to data and from where, organizations can identify data security risks, as well as actionable recommendations on how to reduce that risk.
The 8 Challenges of Data Security
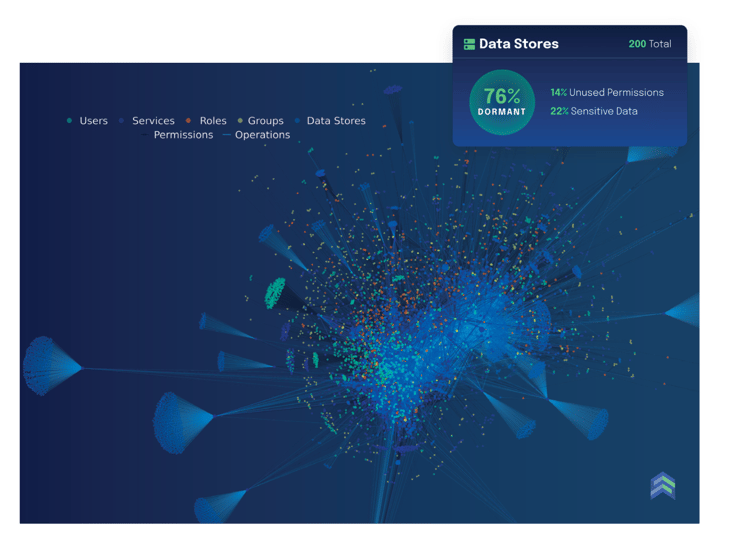
1. Lack of Data Inventory
Organizations simply don’t know what data
they have, where it is, or why it is important.
2. Dormant Data Stores
They’re old, unused, and potentially ripe for an attack because no one’s paying attention.
3. Over-Privileged Data Stores
Just like over-privileged identities, an over-privileged data store has widespread access enabled, inviting trouble.
4. Dormant Identities
The single most common data security issue and one of the overlooked paths to breaches and attacks.
5. Over-Privileged Identities
It’s common for organizations to overestimate the level of access and privilege an identity needs.
6. Delayed or Incomplete Employee & Vendor Offboarding
TBC’s engineers have discovered instances where departed vendors or employees still retain admin-level access to sensitive systems and data. We think you can pretty much guess the risks.
7. Inadequate Segregation of Duties between Development, Test & Production Environments
Companies often fail to enforce segregation of duties between development, test, and production environments.
8. Application & Backup Misconfiguration
There are a lot of ways applications, systems, or backups can be misconfigured. TBC often sees things like inadequate access controls, unprotected files and directories, and access to unnecessary or unused features.
How DSPM and DataGuard Work
Understand how DSPM works and how it can offer full visibility into data stores, including the location of sensitive data, who has access to it, and what operations have been performed against it. Download our Ebook to learn more.
Download the EBook
If you’re ready to secure data more effectively than the current patchwork of traditional security tools like data loss prevention (DLP), data activity monitoring (DAM), and cloud infrastructure entitlement management (CIEM), download our Ebook and learn how DSPM and DataGuard can help. Fill out the form to receive the EBook.


